GR:Gravity/Server/Setup/Reverse Proxy Server
Reverse Proxy Servers & Gravity HTTP/HTTPS setup
For those environments where a Reverse Proxy will be used to handle incoming HTTP(s) requests for the Gravity server, these environments will require an adapted Gravity configuration with respect to HTTP and or HTTPS settings. The following paragraphs will explain in detail how to configure Gravity to run behind a Reverse Proxy server. We will be using the Reverse Proxy server Nginx as the example Reverse Proxy engine.
Nginx configuration
Below is the example host Nginx configuration we will be using:
server {
listen 80;
server_name server.name.com;
return 301 https://$host$request_uri;
}
server {
listen 443 ssl;
server_name server.name.com;
add_header Strict-Transport-Security "max-age=31536000";
location = / {
return 301 /gravity/wm;
}
location / {
proxy_pass http://localhost:36170;
}
}
Here you can see that there is also a server section for secure connections (listen 443 ssl). The ‘Strict-Transport-Security’ header has also been set which enforces HTTP requests to be redirected to HTTPS. With the proxy_pass setting all requests are passed to the Gravity internal web application server running on port 36170 using protocol HTTP.
In the above example configuration it is assumed that the SSL certificate configuration has been set in the Nginx server configuration file: /etc/nginx/conf.d/server.conf, for example:
ssl_certificate /home/admin/ssl/certificate.crt;
ssl_certificate_key /home/admin/ssl/certificate.key;
server {
error_log /var/log/nginx/gravity.zone.log debug;
rewrite_log
}
Gravity configuration
To configure Gravity to work with the above Nginx configuration there are 2 configuration properties that can be set and 1 property that needs to be left out from the Gravity configuration file: _config_admin_config.properties (located in the .../.data/store directory).
- web.http.proxy.port=80, this property defines the port the Reverse Proxy is listening on for HTTP requests (see above Nginx configuration, 'listen 80').
- web.https.proxy.port=443, this property defines the port the Reverse Proxy is listening on for HTTPS requests (see above Nginx configuration 'listen 443').
- web.https.port=..., If this property is configured then it should be removed from the configuration.
For example a Gravity configuration will look something like the following:
# Please do not update or remove the private properties starting with a '.'. # When updating store.user.password set the password as clear text (will be encrypted on startup) # Wed Jan 11 05:03:50 CET 2017 store.user.name=hm store.target.database=MySQL .discovery.disabled=true server.contact.name=hm.gravity.zone store.database.version=7.0.0 store.history.use.database.time=true store.database.name=hm store.history.auditing.on=false store.user.password=ienc(32984902983029830982342765237654726354) osgi.console.port=36171 web.https.proxy.port=443 web.rest.protocol=https store.configuration.home=true store.port.number=3306 store.isdefault=true web.rest.server.port=443 web.http.proxy.port=80 web.http.port=36170 .server.host.name=gravity.zone store.server.name=hm.gravity.zone configuration.general.name=gravity.zone.gravity.store web.rest.host.name=hm.gravity.zone discovery.server.host.address= store.tables.create=true store.history.tables.drop=false server.type.name=saoserver
Note that, as already mentioned, web.https.port is not set. It is important to not set this property as it will otherwise force the Gravity internal web application server to setup its own HTTPS/SSL certificate handling (which is already being taken care of by Nginx).
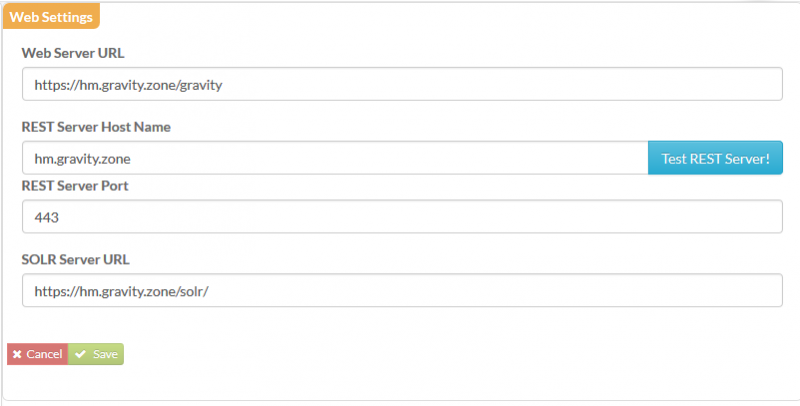
From the Gravity UI the Web configuration should look like this:
Although the Gravity Jetty server itself does not handle the SSL side of HTTPS requests for Solr or RESt, it is still required to set these values as the initial location through which the requests will be accepted in Nginx.