OCTO:Installing the Docker image on a Windows system
Running Octo in Docker-Desktop
The requirement for this setup is as follows:
- Docker-Desktop installed and running with WSL 2 enabled (see https://docs.docker.com/desktop/features/wsl)
- From Octo Downloads (Milestones or Nightly, depending on which version is needed), download the zipped tar and zipped scripts. As of writing the latest were octoserver_docker_kube-lin64-1.3.4_2025-06-30_17-40-31.zip (tar) and octoserver_docker_kube-yaml-1.3.4_2025-06-30_17-40-31.zip (scripts).
Octoserverk Image location
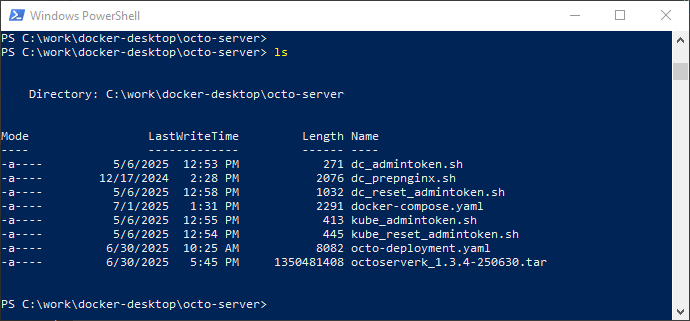
To use the Octo docker-compose.yaml in Docker-Desktop you need to setup a project directory from where the docker-compose for Octo will be started, for example c:/work/docker-desktop/octo-server. At this point you also should probably switch to this directory.
Unpack the zip files to the project directory (for example with the File Explorer or 7Zip).
From here on docker commands are run from a Windows powershell terminal in the project directory setup for the octo-server. The project directory should look something like this:
Before running the docker-compose command the octoserverk image must be available in the local docker repository. This can be done by using the octoserverk image (tar) or by pulling the image from the Harbor docker repository, which requires an enabled Harbor user.
Image load from remote location (pull from Harbor)
From the project directory do a docker login to the Harbor docker repository with:
docker login -u ?username? harbor.remainsoftware.com
After a successful login you can pull the latest octo image with the command
docker pull harbor.remainsoftware.com/octo-nightly/octoserverk:latest
After a successful pull the octoserverk image will be available in the local docker repository. To be able to use this image you will need to change the image definition used in the docker-compose.yaml to:
image: harbor.remainsoftware.com/octo-nightly/octoserverk:latest
Image load from local location
If you are not going to pull the Octo image from the Harbor docker repository then you do not need to change the image name in the docker-compose.yaml. But you do need to manually load the octoserverk image into the local docker repository. The docker command to do this is, is for example:
docker load -i octoserverk_1.3.4-250630.tar
Octo HTTP/HTTPS configuration
The HTTP/HTTP configuration might need to be updated if you want to test Octo locally using the HTTP protocol. By default, the HTTP/HTTPS setting is set to https-only, which will not allow the http protocol to be used with Octo. For local testing the docker-compose configuration for HTTP/HTTPS can be set to the following (see changes in bold):
ENABLE_HTTP: true # defaults to true if not set and NGINX_SUPPORT is enable ENABLE_HTTPS: true # defaults to true if not set and NGINX_SUPPORT is enable... ENABLE_HTTPS_ONLY: false # defaults to true if not set and NGINX_SUPPORT is enable... HTTPS_ONLY_PORT: 8443 # defaults to 443 else assign to the nginx configured https port CERT_HOSTNAME: localhost # for HTTPS leave empty if already providing certificates...
The above HTTP/HTTPS configuration will allow the use of HTTP and HTTPS, albeit HTTPS support (with a self-signed certificate) will not be available in all browsers even if the Octo server public certificate has been imported. Most browsers will allow you to continue use HTTPS but by adding an exception for the site. If you need the certificate then you can copy it to the local directory with the command: “docker-compose cp octo-service:/opt/remain/octo-server/nginx/ssl/tls.crt .”. Even with a certificate, experience is that chromium-based browsers are a problem. Firefox and Opera allow you to continue by setting a site exception.
Running the Octo-server container
When the image is available in the local docker repo and the correct image name is defined in the docker-compose.yaml, then the Octo container can be started with the command “docker-compose up -d”. With the command “docker-compose logs” you can check if the startup was successful (the container console output can also be viewed from the Docker-Desktop UI). The output will look something like this:
octo-nginx | /docker-entrypoint.sh: /docker-entrypoint.d/ is not empty, will attempt to perform configuration
octo-nginx | /docker-entrypoint.sh: Looking for shell scripts in /docker-entrypoint.d/
octo-nginx | /docker-entrypoint.sh: Launching /docker-entrypoint.d/10-listen-on-ipv6-by-default.sh
octo-nginx | 10-listen-on-ipv6-by-default.sh: info: /etc/nginx/conf.d/default.conf is not a file or does not exist
octo-nginx | /docker-entrypoint.sh: Sourcing /docker-entrypoint.d/15-local-resolvers.envsh
octo | 2025-06-30 10:40:06 INFO: initiating Octo app startup, user: octousr, current-dir: /opt/remain/octo-serverocto-nginx | /docker-entrypoint.sh: Launching /docker-entrypoint.d/20-envsubst-on-templates.sh
octo-nginx | /docker-entrypoint.sh: Launching /docker-entrypoint.d30-tune-worker-processes.sh
octo-nginx | /docker-entrypoint.sh: Configuration complete; ready for start up
octo-nginx | 2025/06/30 08:40:06 [notice] 1#1: using the "epoll" event method
octo-nginx | 2025/06/30 08:40:06 [notice] 1#1: nginx/1.29.0
octo-nginx | 2025/06/30 08:40:06 [notice] 1#1: built by gcc 14.2.0 (Alpine 14.2.0)
octo-nginx | 2025/06/30 08:40:06 [notice] 1#1: OS: Linux 5.15.167.4-microsoft-standard-WSL2
octo-nginx | 2025/06/30 08:40:06 [notice] 1#1: getrlimit(RLIMIT_NOFILE): 1048576:1048576
octo-nginx | 2025/06/30 08:40:06 [notice] 1#1: start worker processes
octo-nginx | 2025/06/30 08:40:06 [notice] 1#1: start worker process 20
octo-nginx | 2025/06/30 08:40:06 [notice] 1#1: start worker process 21
octo-nginx | 2025/06/30 08:40:06 [notice] 1#1: start worker process 22
octo-nginx | 2025/06/30 08:40:06 [notice] 1#1: start worker process 23
octo-nginx | 2025/06/30 08:40:06 [notice] 1#1: start worker process 24
octo-nginx | 2025/06/30 08:40:06 [notice] 1#1: start worker process 25
octo-nginx | 2025/06/30 08:40:06 [notice] 1#1: start worker process 26
octo-nginx | 2025/06/30 08:40:06 [notice] 1#1: start worker process 27
octo-nginx | 2025/06/30 08:40:06 [notice] 1#1: start worker process 28
octo-nginx | 2025/06/30 08:40:06 [notice] 1#1: start worker process 29
octo | 2025-06-30 10:40:06 INFO: creating server_conf.json in /opt/remain/octo-server/config
octo-nginx | 2025/06/30 08:40:06 [notice] 1#1: start worker process 30
octo | 2025-06-30 10:40:06 INFO: creating db_conf.json in /opt/remain/octo-server/config
octo | 2025-06-30 10:40:06 INFO: creating access_token.js in /opt/remain/octo-server/config
octo | 2025-06-30 10:40:06 INFO: NGINX_SUPPORT: enable
octo | 2025-06-30 10:40:06 INFO: ENABLE_HTTP: false
octo | 2025-06-30 10:40:06 INFO: ENABLE_HTTPS: false
octo | 2025-06-30 10:40:06 INFO: ENABLE_HTTPS_ONLY: true
octo | 2025-06-30 10:40:06 INFO: HTTPS_ONLY_PORT: 8443
octo-nginx | 2025/06/30 08:40:06 [notice] 1#1: start worker process 31
octo-nginx | 2025/06/30 08:40:06 [notice] 1#1: start worker process 32
octo-nginx | 2025/06/30 08:40:06 [notice] 1#1: start worker process 33
octo-nginx | 2025/06/30 08:40:06 [notice] 1#1: start worker process 34
octo-nginx | 2025/06/30 08:40:06 [notice] 1#1: start worker process 35
octo-nginx | 2025/06/30 08:40:06 [notice] 1#1: start worker process 36
octo-nginx | 2025/06/30 08:40:06 [notice] 1#1: start worker process 37
octo-nginx | 2025/06/30 08:40:06 [notice] 1#1: start worker process 38
octo-nginx | 2025/06/30 08:40:06 [notice] 1#1: start worker process 39
octo | 2025-06-30 10:40:06 INFO: creating tls certificate and key for host: 'devkube' in directory: /opt/remain/octo-server/nginx/ssl
octo | Generating a RSA private key
octo | .....+++++
octo | .....+++++
octo | writing new private key to '/opt/remain/octo-server/nginx/ssl/tls.key'
octo | -----
octo | 2025-06-30 10:40:06 INFO: installing default Octo-Nginx HTTPS configuration
octo | 2025-06-30 10:40:06 INFO: installing default Octo-Nginx HTTP to HTTPS redirect configuration
octo | 2025-06-30 10:40:06 INFO: update HTTPS port number on HTTP redirect, port: 8443
octo | 2025-06-30 10:40:06 INFO: updating file permission of Nginx configurations
octo | 2025-06-30 10:40:06 INFO: start MongoDB on port 27017, log-file: /opt/remain/octo-server/log/mongodb.log
octo | 2025-06-30 10:40:06 INFO: MongoDB started on PID: 68
octo | 2025-06-30 10:40:11 INFO: check availability of MongoDB...
octo | 2025-06-30 10:40:12 INFO: MongoDB is available
octo | 2025-06-30 10:40:12 INFO: starting cron for background job processing
octo | 2025-06-30 10:40:12 INFO: creating backup.env in /opt/remain/octo-server/config/env
octo | 2025-06-30 10:40:12 INFO: starting node server.js in: /opt/remain/octo-server/server
octo | 2025-06-30T10:40:12.303 [INFO] [default] log4js setup completed, log file: /opt/remain/octo-server/log/octo.log
octo | 2025-06-30T10:40:12.981 [INFO] [Store Service] Octo Admin DB trying to connect...
octo | 2025-06-30T10:40:12.982 [INFO] [Store Service] Octo Admin Database name: octo
octo | 2025-06-30T10:40:13.361 [INFO] [Octo Server] Octo Server started
octo | 2025-06-30T10:40:13.362 [INFO] [Octo Server] Octo Server available on http://172.18.0.2:47007
octo | 2025-06-30T10:40:13.370 [INFO] [Store Service] Octo Admin DB connected successfully!
octo | 2025-06-30T10:40:13.370 [INFO] [Store Service] MongoDB Driver Version: 6.10.0
octo | 2025-06-30T10:40:13.370 [INFO] [Store Service] Mongoose Version: 6.13.8
octo | 2025-06-30T10:40:13.378 [INFO] [Store Service] MongoDB Server Version: 6.0.9
octo | 2025-06-30T10:40:13.386 [INFO] [Store Service] MongoDB Server Compatibility Version: 6.0
octo | 2025-06-30T10:40:13.387 [WARN] [Store Service] MongoDB Server Compatibility Version (6.0) does not match the MongoDB Server Version (6.0.9)
octo | 2025-06-30T10:40:13.389 [INFO] [Session Log Service] Checking sign-in logs to purge...
octo | 2025-06-30T10:40:13.393 [WARN] [Configuration Service] checkProductConfig() Failed to initialize the host name because the product configuration doesn't exist! This warning should not appear once you configure and save the email SMTP server settings using Octo Admin > Email.
octo | 2025-06-30T10:40:13.395 [INFO] [Tenant Service] Initializing tenants...
octo | 2025-06-30T10:40:13.395 [INFO] [Tenant Service] Initializing tenants... Found: 0 organizations
octo | 2025-06-30T10:40:13.395 [INFO] [Tenant Service] Initializing tenants... Done!
octo | 2025-06-30T10:40:13.396 [INFO] [Session Log Service] Checking sign-in logs to purge... No configurations found! Reverting to default settings.
octo | 2025-06-30T10:40:13.396 [INFO] [Session Log Service] Purging 'failed' sign-ins logs older than 365 days...
octo | 2025-06-30T10:40:13.397 [INFO] [Session Log Service] Purging 'successful' sign-ins logs older than 365 days...
octo | 2025-06-30T10:40:13.399 [INFO] [Session Log Service] Purged 0 'successful' sign-in logs.
octo | 2025-06-30T10:40:13.399 [INFO] [Session Log Service] Purging 'successful' sign-in logs to purge... Done
octo | 2025-06-30T10:40:13.399 [INFO] [Session Log Service] Purged 0 'failed' sign-in logs.
octo | 2025-06-30T10:40:13.399 [INFO] [Session Log Service] Purging 'failed' sign-in logs to purge... Done
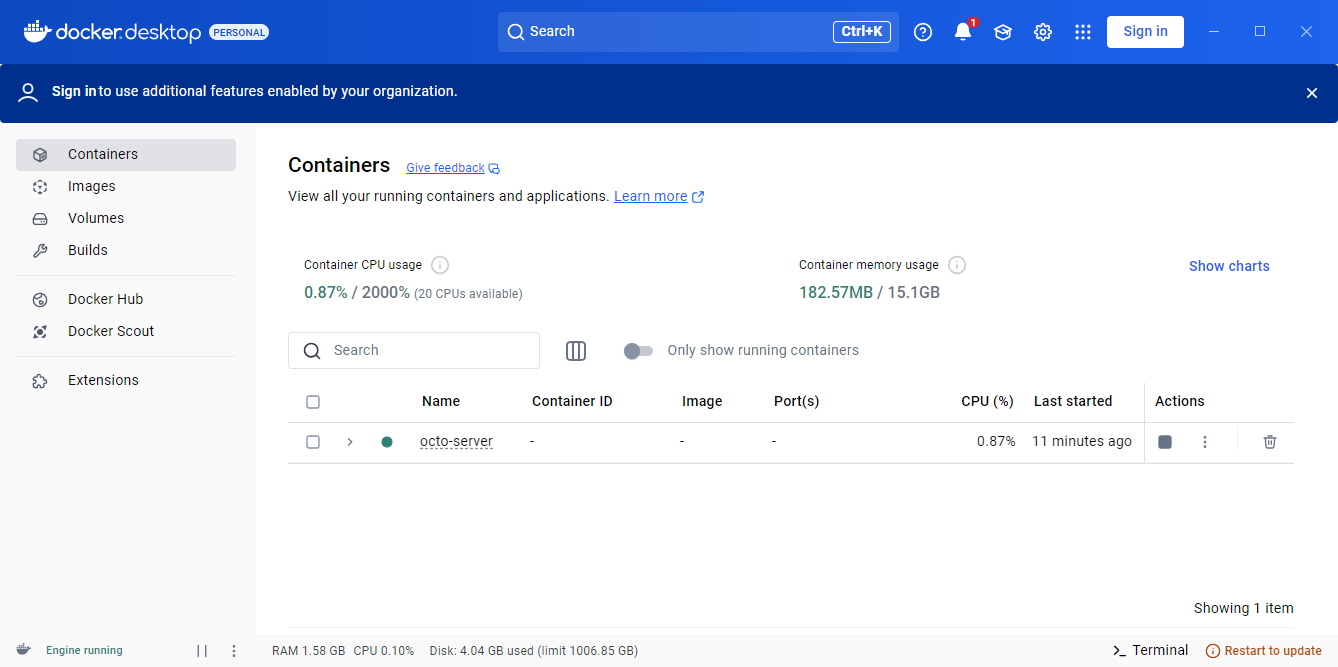
Docker-Desktop will show the following:
First task in the Octo-server setup is the configuration of the email data. To be able to do this a user has to be registered, followed by a login with the registered username using the Octo server admin token as the password.
Get the Octo admin token
The admin token can be retrieved using the script dc_admintoken.sh (in the same zip file as the docker-compose.yaml). Once the script is run with: ‘./ dc_admintoken.sh’, the file admin.token will be created in the project directory, the created file will contain the password (token) that can be used for an admin login. If you do not have the dc_admintoken.sh script readily available, you can use the command:
docker-compose exec octo-service grep "exports.ADMIN_ACCESS_TOKEN =" /opt/remain/octo-server/config/access_token.js
The output of this command will be similar to the text below:
exports.ADMIN_ACCESS_TOKEN = "fa4dbe12-a826-49d8-9377-649a2b518c32";
The admin token will be the quoted id but without the quotes.
For here on Octo is available from a web browser, either as http://localhost:8080 or https:/localhost:8443 (using Firefox or Opera).
Vulnerabilities with status high
Qs 6.5.3 CVE-2022-24999
+-- express@4.18.2 | +-- body-parser@1.20.1 | | `-- qs@6.11.0 deduped | `-- qs@6.11.0 `-- request@2.88.2 `-- qs@6.5.3
Summary qs before 6.10.3 allows attackers to cause a Node process hang because an __ proto__ key can be used. In many typical web framework use cases, an unauthenticated remote attacker can place the attack payload in the query string of the URL that is used to visit the application, such as a[__proto__]=b&a[__proto__]&a[length]=100000000. The fix was backported to qs 6.9.7, 6.8.3, 6.7.3, 6.6.1, 6.5.3, 6.4.1, 6.3.3, and 6.2.4.
Note that the vulnerability has been fixed and back ported to qs version 6.5.3 (and others, see https://github.com/ljharb/qs/pull/428), the back ported and safe version is being used in Octoserver as a dependency of request 2.88.2.
Dicer 0.3.1 CVE-2022-24434
+-- dicer@0.3.1
Summary This affects all versions of package dicer. A malicious attacker can send a modified form to server, and crash the nodejs service. A complete denial of service can be achieved by sending the malicious form in a loop.
There is no fix available for this issue. We are working on replacing dicer.
A word on sending modified data and prototype pollution vulnerability as is possible with the javascript __proto__ key.
The way Octoserver interacts with the back-end is not sensitive to how prototype pollution can be applied i.e. an unauthenticated request in which a javascript __proto___ key is injected into the request payload. With Octoserver every back-end call is authenticated by a token in the supplied request, unauthenticated requests will not be processed, furthermore all Octoserver requests are backed by a REST API which fully sanitize input requests and make it impossible to manipulate the request data to have the API execute unauthorized actions or exploit security vulnerabilities.